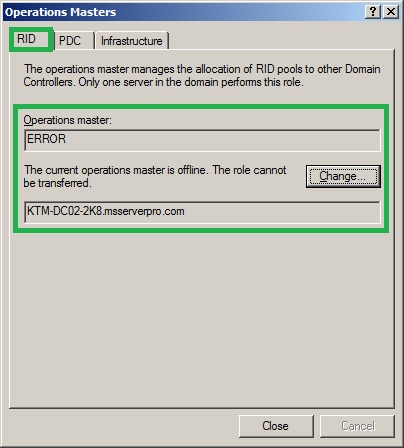
Computer object commands
List all computer accounts in a domain
Get-ADComputer –Filter {Name –Like "*"}
View all computers that are logged in for 90 days to the Active Directory
Search-ADaccount -AccountInactive -Timespan 90 -ComputersOnly
OR
$lastLogon = (get-date).adddays(-90).ToFileTime()
Get-ADComputer -filter {lastLogonTimestamp -gt $lastLogon}
Find and delete all disabled Computer accounts in Active Directory
Search-ADAccount -AccountDisabled -ComputersOnly | Sort-Object | Remove-ADComputer
Find and delete disabled computer accounts from a specific OU
Search-ADAccount -AccountDisabled -Searchbase "OU=IT,DC=Contoso,DC=Com" -ComputersOnly | Sort-Object | Remove-ADComputer
Find and delete all computer accounts that no longer have signed up since 11/20/2011 to the Active Directory
Search-ADAccount -AccountInactive -DateTime "20.11.2011" –ComputersOnly | Sort-Object | Remove-ADComputer
List only disabled Computer accounts in Domain
Search-ADAccount -AccountDisabled -ComputersOnly | Format-Table Name
Move Computer to other OU (example: Computer=CLIENT1 to OU=IT)
Get-ADComputer CLIENT1 | Move-ADObject -TargetPath "OU=IT,DC=Contoso,DC=Com"
See Computer account detail (example: Computer=CLIENT1)
Get-ADComputer -Filter {Name -Like "CLIENT1"}
Get a specific computer showing all the properties (example: Computer=CLIENT1)
Get-ADComputer "CLIENT1" -Properties *
List Computers (Name, Operating System, Service Pack, Operating System version)
Get-ADComputer -Filter * -Property * | Format-Table Name,OperatingSystem,OperatingSystemServicePack,OperatingSystemVersion -Wrap –Auto
Export Computers List (Name, Operating System, Service Pack, Operating Systemversion)to CSV File
Get-ADComputer -Filter * -Property * | Select-Object Name,OperatingSystem,OperatingSystemServicePack,OperatingSystemVersion | Export-CSV AllWindows.csv -NoTypeInformation -Encoding UTF8
Get Computer IPv4 Address and DnsHostName
Get-ADComputer -Filter {Name -Like "Computer-Name"} -Properties IPv4Address | Format-List Name,DnsHostName,IPv4Address
Get all Computers in a specific OU (example: OU=IT, Domain=Contoso.com)
Get-ADComputer -SearchBase "OU=IT,DC=Contoso,DC=Com" -filter *
Get all the Computers without a specific DNS suffix
Get-ADComputer -filter "DnsHostName -notlike '*.Contoso.Com'"
Get Computer Service Principal Names (SPNs)
Get-ADComputer "Computer-Name" –Properties ServicePrincipalNames | Select-Object –Expand ServicePrincipalNames
Get Computers Security Identifiers (SIDs)
Get-ADComputer -Filter {Name -like "*"} | Select Name,SID | Format-Table -Auto
All computer accounts that were created in the last 90 days in the Active Directory
Get-ADComputer -Filter * -Properties whenCreated | ? { ((Get-Date) - $_.whenCreated).Days -lt 90} | Format-Table Name,WhenCreated,Name,DistinguishedName -Autosize -Wrap
All computer accounts that were created as of December 1, 2011 (12/01/2011) in the Active Directory
Get-ADComputer -LDAPFilter "(&(objectCategory=person)(whenCreated>=20111201000000.0Z))" -Properties whenCreated | Format-Table Name,whenCreated,distinguishedName -Autosize -Wrap
All computer accounts that were created here in a given time, between the 10/01/2011 and 12/01/2011 in Active Directory
$Start = Get-Date -Day 01 -Month 10 -Year 2011 -Hour 00
$End = Get-Date -Day 01 -Month 12 -Year 2011 -Hour 23 -Minute 59
Get-ADComputer -Filter * -Properties whenCreated | ? { ($_.whenCreated -gt $Start) -and ($_.whenCreated -le $End) } | Format-Table Name,WhenCreated,DistinguishedName -Autosize -Wrap
All computer accounts, Last Password Set in a given time, between the 10/01/2011 and 12/01/2011 in Active Directory
$Start = Get-Date -Day 01 -Month 10 -Year 2011 -Hour 00
$End = Get-Date -Day 01 -Month 12 -Year 2011 -Hour 23 -Minute 59
Get-ADComputer -Filter * -Properties PasswordLastSet | ? { ($_.PasswordLastSet -gt $Start) -and ($_.PasswordLastSet -le $End) } | Format-Table Name,WhenCreated,DistinguishedName -Autosize -Wrap
All computer accounts, Last Password Set in the last 90 days in Active Directory
$Date = (Get-Date).AddDays(-90)
Get-ADComputer -Filter * -Properties PasswordLastSet | where { $_.PasswordLastSet -le $Date } | Format-Table Name,PasswordLastSet,DistinguishedName -Autosize -Wrap
Group object commands
List all members of a group (example: Group=Experts)
Get-ADGroupMember Experts | Format-Table Name
All properties of a group (example: Group=IT)
Get-ADGroup IT -Properties *
List only Universal Security groups
Get-ADGroup –LDAPFilter "(&(objectCategory=group)(groupType:1.2.840.113556.1.4.803:=-2147483640))"
List only Global Security groups
Get-ADGroup –LDAPFilter "(&(objectCategory=group)(groupType:1.2.840.113556.1.4.803:=-2147483646))"
List only Domain Local Security groups
Get-ADGroup –LDAPFilter "(&(objectCategory=group)(groupType:1.2.840.113556.1.4.803:=-2147483644))"
List all Group memberships for a user (example: User=EdPrice)
Get-ADAccountAuthorizationGroup EdPrice
Move a Group to another OU (example: Group=Experts, Old-OU=IT, New-OU=Service, Domain=Contoso.com)
Move-ADObject "CN=Experts,OU=IT,DC=Contoso,DC=com" -TargetPath "OU=Service,DC=Contoso,DC=com"
Move-ADObject "CN=Experts,OU=IT,DC=Contoso,DC=com" -TargetPath "OU=Service,DC=Contoso,DC=com"
Add members to a group (example: Group=Experts, User=EdPrice)
Add-ADGroupmember Experts -Member EdPrice
Delete Group (example: Group=Experts)
Remove-ADGroup Experts
Delete a User from a Group (example: Group=Experts, User=EdPrice)
Remove-ADGroupMember Experts -Member EdPrice
Set Description for a Group (example: Group=JoinPC, Description=This group is allowed join PCs to Domain)
Set-ADGroup JoinPC -Description "This group is allowed join PCs to Domain"
Add Users from one Group to another Group (example: from Group1=DataUsers to Group2=SQLUsers)
Get-ADGroupMember DataUsers | Select sAMAccountName | ForEach { Add-ADGroupMember SQLUsers -Members $_.sAMAccountName }
Comparing two Groups to see the Group memberships (example: Group1=Administratorso, Group2=DNSAdmins)
Compare-Object ( Get-ADGroupMember Administrators) ( Get-ADGroupMember DNSAdmins) -IncludeEqual
Organizational Unit (OU) commands
All OUs in Domain
Get-ADOrganizationalUnit -Filter {Name -like „*“} | FT Name, DistinguishedName -A
Create OU (example: OU=IT, Domain=Contoso.com)
New-ADOrganizationalUnit -Name IT -Path "DC=Contoso,DC=Com"
Contents of a specific OU (example: OU=IT, Domain=Contoso.com)
Get-ADObject -Filter {Name -Like "*"} -Searchbase "OU=IT,DC=Contoso,DC=Com"
Rename OU (example: Old-Name=IT, New-Name=Admin, Domain=Contoso.com)
Rename-ADObject "OU=IT,DC=Contoso,DC=Com" -NewName Admin
Delete OU including contents (example: OU=IT, Domain=Contoso.com)
Remove-ADOrganizationalUnit IT -Recursive
Delete user from specific OU (example: User=EdPrice, OU=IT, Domain=Contoso.com)
Remove-ADObject "CN=EdPrice,OU=IT,DC=Contoso,DC=Com"
Move all objects from one OU to another OU (example: Old-OU=IT, New-OU=Manager, Domain=Contoso.com)
Get-ADObject -Filter {Name -Like "*"} -Searchbase "OU=IT,DC=Contoso,DC=Com" -SearchScope OneLevel | Move-ADObject -TargetPath "OU=Manager,DC=Contoso,DC=Com"
User object commands
List all User accounts in the Domain
Get-ADUser –Filter *
List all User accounts in a specific OU (example: OU=IT, Domain=Contoso.com)
Get-ADUser –Filter * -Searchbase "OU=IT,DC=Contoso,DC=Com" | FT
List all User accounts from specific City (example: City=NewYork)
Get ADUser -Filter {city - like "NewYork"} | FT
List only disabled User accounts in Domain
Search-ADAccount –AccountDisabled –Usersonly | FT Name
List all User accounts whose First Name is Ed
Get-ADUser –Filter {givenName –Like "Ed"} | FT
List all User accounts whose Last Name is Price
Get-ADUser –Filter {Surname –Like "Price"} | FT
List all User accounts from the specific Department (example: Department=Support)
Get-ADUser –Filter {Department –Like "Support"} | FT
List a User's Group memberships (example: User=Richard)
Get-ADPrincipalGroupMembership -Identity Richard
List all Users from specific Group and move Users to another OU (example: Group=People, Target OU=NewYork, Domain=Contoso.com)
Get-ADGroupMember People -Recursive | Move-ADObject –TargetPath "OU=NewYork,DC=Contoso,DC=Com"
Remove all users in an OU from a specific Group (example: Group=People, OU=NewYork, Domain=Contoso.com)
$Users = Get-ADUser -Filter * -Searchbase "OU=NewYork,DC=Contoso,DC=Com"
Remove-ADGroupMember -Identity People -Member $Users -Confirm:0